I wanted to keep the Windows 2000 install that came on my new laptop and install Windows XP, but Dell only created one large NTFS partition. After doing a little searching around, I found ntfsresize, part of the Linux NTFS Project.
After downloading and burning the SystemRescueCD, I popped it in the drive, booted off it and typed run_qtparted hit enter and happily pointed and clicked my way through resizing the existing NTFS partition to free up some space for XP. And maybe even Gentoo
Category Archives: Housing
New Laptop
My aging and well traveled Dell Latitude C800 is up for replacement, so we ordered 3 identical Dell Latitude D800s. Fully decked out, with the kickass video card and the giant monitor (1920×1200 baby), dual batteries, DVD+R burner, etc.
They were ordered with Windows 2000 preinstalled (for the tech support) and a Windows XP license, but I’m considering wiping mine and installing Windows XP and gentoo. I’ve only got a few things installed so far, so not a big deal either way.
Another annoying Mozilla bug
Every once in a while, while using Firefox, it sits there hung trying to resolve the ip address of something that isn’t in DNS. This happened twice in 10 minutes today, so I went searching bugzilla for an answer, and I found an open bug.
Its gotten about as much activity as the last bug I blogged about.
Port 445 worm details revealed
After spending the last few days watching portsentry logs for repeat offenders and moving them off to the quarantine VLAN, I finally got the chance to analyze an infected machine when one of Housing’s seldom used (and even less frequently updated) laptops was connected and got infected.
While installing Windows updates (MS04-011, MS04-012, MS04-014, MS04-016, etc) , the user saw an LSASS.EXE error and a shutdown counter started. The updates finished installing before the restart, but it was still infected. After rebooting and updating the McAfee virus scanner from 4387 to 4388 DATs, it detected c:winntsystem32bling.exe as W32/Sdbot.worm, which is what we’ve assume it to be all along.
The exe name seems to be pretty random, though one of the more common ones we’ve seen is winsmc.exe. Another recent virus that exhibits similar behavior is W32/Sasser.worm.g, so we are probably seeing some of that as well.
I can pretty much narrow down the exploit to using something that is patched in MS04-011, 012, or 014, as I have another laptop that has those patches, but nothing later and has not been infected. Most likely MS04-011, with the LSASS fixes. Since all these patches are from April of this year, the moral of the story is to visit Windows Update on a regular basis, or turn on Automatic Updates if you are on a high speed connection.
Network bad, quarantine good
Well, as previously mentioned, I’ve been disabling URHnet connections like a fiend and yesterday was no exception: about 60 between 9 am and 4 pm and another 40 or so last night. All of this is due to some piece of malware that none of the anti-virus vendors seem to be catching yet. With the rate of change on the sdbot family, I’m not all that suprised.
One thing that’s different this year is that we’re not really disabling the connections, they are being moved to a network that has no connection to the outside world, called the “quarantine vlan”. There is just one DHCP server/DNS server/web server/ftp server machine, with a few instructions for the residents and some tools for our NetTechs to use. Thanks to some hard work by the fine people at CITES backbone and LAN maintenance groups, NetTechs have the ability to change which network a room is on from a webpage. So, really, no more disabled rooms, unless they are doing something Really Bad.
Disabling ports
Well, I survived opening. Now I’ve moved on to disabling random URHnet ports that have virus and worm infected machines connected to them. I think I turned off somewhere around 80 rooms today.
And, on a completely unrelated note, I must resist the urge to build a new computer, but how can I with such flashy new hardware available?
We are open for business
This is the earliest we’ve ever opened the labs and, knock on wood, this is the smoothest one I’ve had in some time. Very few people are actually here,
The only bump in the road was easily solved, once I thought it through: URHNet users were getting told that our print servers didn’t have drivers for the printers we were sharing. This is not true. Since they are coming in as the Guest account, I figured something had to be up with permissions. The share (servernameprint$) had Read permissions for Everyone, so that’s good. The underlying file permissions, on the other hand, were missing Everyone. So, I re-added that, and all is now good.
And, had I looked in the Microsoft Knowledgebase first, I would have found article 271901.
HP 5308xl and port security
Since my searches on Google came up dry, here’s how you clear existing MAC addresses from port security on an HP ProCurve 5308xl (from pg 237 of the Access Security Guide):
#configure terminal
(config)#show port-security H6
(config)#no port-security H6 mac-address 00b0d0-46b139
(config)#show port-security H6
Copy and paste of the MAC from the output of the show command works just fine.
Lab installs
I’ve been busy rebuilding lab machines, hammering the network, as this graph shows: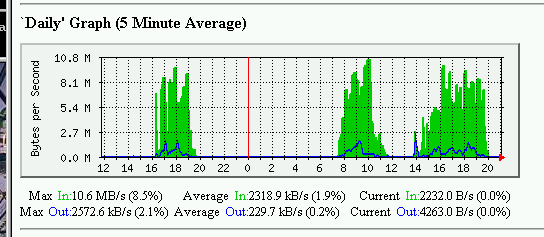
That’s the gig interface on a Dell 2650 server, working hard. And those spikes correspond to about 120 workstation installs across 5 sites. Graduate sites, that have to be scheduled, start tommorrow morning.
And we get to find out how people are going to react to losing the (free) dot printers. With cheaper laser printing, more lasers and color lasers available in 3 sites, hopefully it will go well.
Been kind of quiet around here
Working my tail off, getting ready for opening, as usual. Lab rebuilds are progressing nicely, close to go time, but I should probably roll in the latest (out of cycle) security bulletin from Microsoft first. Hopefully it doesn’t require any strange things to install properly. Now I just need to hope for no critical patches on patch Tuesday.
In what will probably be the last chance until September, I took Friday off, and spent most of the day working at Hoopeston, getting my linux desktop closer to moving over to new hardware and other misc tasks. And we had one of those 10 minute tasks turn into an all afternoon clusterf$%k. But, in the long run, it was really just moving up the schedule for a reinstall, not creating work. Yeah, that’s the ticket.
Saturday I took advantage of the wonderful concrete floor and air tools to rotate the tires on the Dakota and spent some time working in Hoopeston again. I picked up Alisha’s new hamster, Stinky, from my in-laws and brought it home. He seems to be happier in his plastic habitat than in the cardboard box. Maybe I’ll get some pictures this week.
